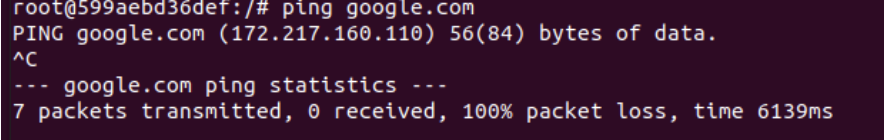
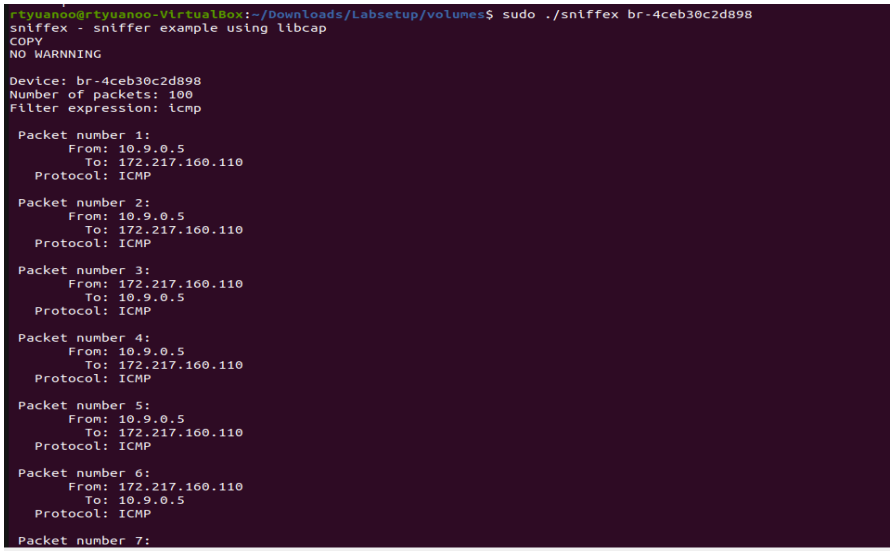
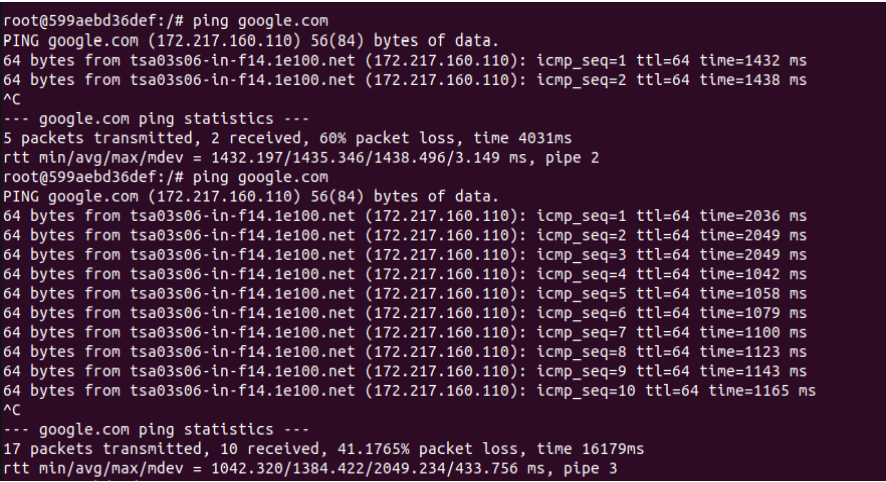
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
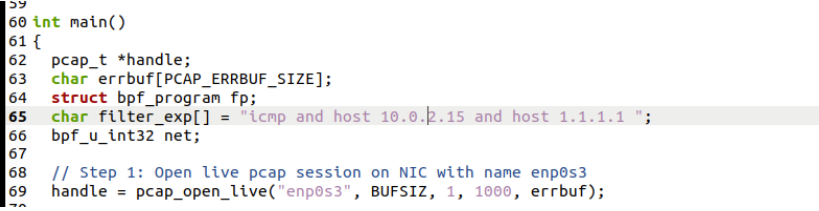
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
| #define APP_NAME "sniffex"
#define APP_DESC "sniffer example using libcap"
#define APP_COPYRIGHT "COPY"
#define APP_DISCLAIMER "NO WARNNING"
#include <pcap.h>
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
#include <ctype.h>
#include <errno.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <netdb.h>
#include <netinet/in_systm.h>
#include <netinet/in.h>
#include <netinet/ip.h>
#include <netinet/ip_icmp.h>
#include <arpa/inet.h>
#define SNAP_LEN 1518
#define SIZE_ETHERNET 14
#define ETHER_ADDR_LEN 6
struct sniff_ethernet
{
u_char ether_dhost[ETHER_ADDR_LEN];
u_char ether_shost[ETHER_ADDR_LEN];
u_short ether_type;
};
struct sniff_ip
{
u_char ip_vhl;
u_char ip_tos;
u_short ip_len;
u_short ip_id;
u_short ip_off;
#define IP_RF 0x8000
#define IP_DF 0x4000
#define IP_MF 0x2000
#define IP_OFFMASK 0x1ffff
u_char ip_ttl;
u_char ip_p;
u_char ip_sum;
struct in_addr ip_src,ip_dst;
};
#define IP_HL(ip) (((ip)->ip_vhl) & 0x0f)
#define IP_V(ip) (((ip)->ip_vhl) >>4)
typedef u_int tcp_seq;
struct sniff_tcp
{
u_short th_sport;
u_short th_dport;
tcp_seq th_seq;
tcp_seq th_ack;
u_char th_offx2;
#define TH_OFF(th) (((th)->th_offx2 & 0xf0) >>4 )
u_char th_flags;
#define TH_FIN 0x01
#define TH_SYN 0x02
#define TH_RST 0x04
#define TH_PUSH 0x08
#define TH_ACK 0x10
#define TH_URG 0x20
#define TH_ECE 0x40
#define TH_CWR 0x80
#define TH_FLAGS
(TH_FIN|TH_SYN|TH_RST|TH_ACK|TH_URG|TH_ECE|TH_CWR)
u_short th_win;
u_short th_sum;
u_short th_urp;
};
struct sniff_icmp {
u_char icmp_type;
u_char icmp_code;
u_short icmp_chksum;
u_short icmp_n;
};
void got_packet(u_char *args,const struct pcap_pkthdr *header,const u_char *packet);
void print_payload(const u_char *payload ,int len);
void print_hex_ascill_line(const u_char *payload,int len,int offset);
void print_app_banner(void);
void print_app_usage(void);
void print_app_banner(void)
{
printf("%s - %s\n",APP_NAME,APP_DESC);
printf("%s\n",APP_COPYRIGHT);
printf("%s\n",APP_DISCLAIMER);
printf("\n");
return;
}
void print_app_usage(void)
{
printf("Usage: %s [interface]\n",APP_NAME);
printf("/n");
printf("Options:\n");
printf(" interface listen on <interface> for packets. \n");
printf("\n");
return;
}
void print_hex_ascill_line(const u_char *payload,int len,int offset)
{
int i;
int gap;
const u_char *ch;
printf("%05d ",offset);
ch = payload;
for (i=0;i<len;i++){
printf("%02x ",*ch);
ch++;
if(i==7){
printf(" ");
}
}
if (len<8){
printf(" ");
}
if (len<16){
gap = 16-len;
for (i=0;i<gap;i++){
printf(" ");
}
}
printf(" ");
ch =payload;
for (i=0;i<len;i++){
if(isprint(*ch))
printf("%c",*ch);
else
printf(".");
ch++;
}
printf("\n");
return;
}
void print_payload(const u_char *payload ,int len)
{
int len_rem = len;
int line_width = 16;
int line_len;
int offset=0;
const u_char *ch = payload;
if (len<=0)
return;
if(len <=line_width)
{
print_hex_ascill_line(ch,len,offset);
return;
}
for ( ; ; ){
line_len = line_width % len_rem;
print_hex_ascill_line(ch,line_len,offset);
len_rem = len_rem - line_len;
ch = ch+ line_len;
offset = offset + line_width;
if(len_rem <= line_width){
print_hex_ascill_line(ch,len_rem,offset);
break;
}
}
return;
}
void send_icmpreply(u_char *packet)
{
const struct sniff_ip *old_ip_header;
old_ip_header = (struct sniff_ip *)(packet + SIZE_ETHERNET);
int ip_len = ntohs(old_ip_header->ip_len);
char buf[ip_len];
bzero(buf,sizeof(buf));
memcpy(buf,(packet + SIZE_ETHERNET),sizeof(buf));
char *ptr = buf;
struct sniff_ip *ip_header = (struct sniff_ip*)(ptr);
int size_ip_header = IP_HL(ip_header)*4;
struct sniff_icmp *icmp_header;
icmp_header = (struct sniff_icmp*)(packet +size_ip_header);
icmp_header->icmp_type = 8;
icmp_header->icmp_chksum = 0;
icmp_header->icmp_n =0 ;
struct in_addr tempAddress = ip_header->ip_dst;
ip_header->ip_dst = ip_header->ip_src;
ip_header->ip_src = tempAddress;
struct sockaddr_in dst;
dst.sin_family = AF_INET;
inet_pton(AF_INET,inet_ntoa(ip_header->ip_dst),&dst.sin_addr.s_addr);
dst.sin_port = htons(0);
icmp_header->icmp_n ++ ;
int one = 1;
int s;
s = socket(AF_INET,SOCK_RAW,IPPROTO_RAW);
setsockopt(s,IPPROTO_IP,IP_HDRINCL,&one,sizeof(one));
sendto(s,buf,sizeof(buf),0,(struct sockaddr *)&dst ,sizeof(dst));
close(s);
}
void got_packet(u_char *args,const struct pcap_pkthdr *header,const u_char *packet)
{
static int count = 1;
const struct sniff_ethernet *ethernet;
const struct sniff_ip *ip;
const struct sniff_tcp *tcp;
const char *payload;
int size_ip;
int size_tcp;
int size_payload;
printf("\n Packet number %d: \n",count);
count++;
ethernet = (struct sniff_ethernet*)(packet);
ip = (struct sniff_ip*)(packet + SIZE_ETHERNET);
size_ip = IP_HL(ip)*4;
if (size_ip<20)
{
printf(" *Invalid IP header length : %u bytes \n",size_ip);
return;
}
printf(" From: %s\n", inet_ntoa(ip->ip_src));
printf(" To: %s\n", inet_ntoa(ip->ip_dst));
switch(ip->ip_p)
{
case IPPROTO_TCP:
printf(" Protocol: TCP\n")
break;
case IPPROTO_UDP:
printf(" Protocol: UDP\n");
return;
case IPPROTO_ICMP:
printf(" Protocol: ICMP\n");
send_icmpreply(packet);
return;
default:
printf(" Protocol: others\n");
return;
}
tcp = (struct sniff_tcp*)(packet + SIZE_ETHERNET + size_ip);
size_tcp = TH_OFF(tcp)*4;
if (size_tcp < 20 )
{
printf(" *Invalid TCP header length : %u bytes \n",size_tcp);
return;
}
printf(" Src port: %d\n",ntohs(tcp->th_sport));
printf(" Dst port: %d\n",ntohs(tcp->th_dport));
payload = (u_char*)(packet + SIZE_ETHERNET +size_ip + size_tcp);
size_payload = ntohs(ip->ip_len) - size_ip - size_tcp;
if ( size_payload >0 )
{
printf(" Payload (%d bytes):\n",size_payload);
print_payload(payload,size_payload);
}
return;
}
int main(int argc, char **argv)
{
char *dev = NULL;
char errbuf[PCAP_ERRBUF_SIZE];
pcap_t *handle;
char filter_exp[] = "icmp";
struct bpf_program fp;
bpf_u_int32 mask;
bpf_u_int32 net;
int num_packets = 100;
print_app_banner();
if(argc == 2 ){
dev = argv[1];
}
else if (argc > 2){
fprintf(stderr, "error:unrecongnized command_line options\n\n" );
print_app_usage();
exit(EXIT_FAILURE);
}
else{
dev = pcap_lookupdev(errbuf);
if(dev = NULL){
fprintf(stderr,"Couldn't find default device: %s\n",errbuf);
exit(EXIT_FAILURE);
}
}
if(pcap_lookupnet(dev,&net,&mask,errbuf) == -1){
fprintf(stderr,"Couldn't get netmask for device %s: %s\n",dev,errbuf);
net = 0;
mask = 0;
}
printf("Device: %s\n",dev);
printf("Number of packets: %d\n",num_packets);
printf("Filter expression: %s\n",filter_exp);
handle = pcap_open_live(dev,SNAP_LEN,1,1000,errbuf);
if(handle == NULL){
fprintf(stderr,"Couldn't open device %s : %s\n",dev,errbuf);
exit(EXIT_FAILURE);
}
if(pcap_datalink(handle) != DLT_EN10MB){
fprintf(stderr,"%s is not an Ethernet\n",dev);
exit(EXIT_FAILURE);
}
if(pcap_compile(handle,&fp,filter_exp,0,net) == -1){
fprintf(stderr,"Couldn't parse filter %s : %s\n",filter_exp,pcap_geterr(handle));
exit(EXIT_FAILURE);
}
if (pcap_setfilter(handle,&fp) == -1)
{
fprintf(stderr,"Couldn't install filter %s : %s\n",filter_exp,pcap_geterr(handle));
exit(EXIT_FAILURE);
}
pcap_loop(handle,num_packets,got_packet,NULL);
pcap_freecode(&fp);
pcap_close(handle);
printf("\n Capture complete. \n");
return 0;}
|